1. Introduction
In the emerging web3 landscape, the need for secure and trustworthy identity solutions has become more important than ever. Enter the concept of Verifiable Credentials that offer a promising solution — allowing individuals and organizations to easily and securely prove their identity, credentials, and qualifications in a trustworthy manner. With the adoption of blockchain increasing steadily, Verifiable Credentials are becoming an essential tool for enabling secure and trusted interactions among individuals, organizations, and machines.
In this blog post, we’ll explore what Verifiable Credentials are, how they work, and why they are so important in the web3 ecosystem along with taking a deep dive into their lifecycle.
Buckle up and let’s explore!
2. A Deep Dive into the Ecosystem
2.1 What are Verifiable Credentials?
As the name suggests, Verifiable Credentials (VCs) are a type of digital identity solution that enable individuals and organizations to verify their identity on the internet. They are a type of digital credential that can represent both physical credentials, like passports and licenses, and non-physical assets, like bank account ownership. They are an open standard that is widely used in digital identity verification. They differ from traditional credentials, such as passports or driver’s licenses, in that they are digitally signed and tamper-proof, allowing them to be shared and verified with confidence.
Let’s make it simpler with an example: Imagine that you’re applying for a job, and the employer needs to verify your educational qualifications and work experience. In the past, you might have had to provide physical copies of your certificates and references, which could be time-consuming and sometimes difficult to authenticate.
With Verifiable Credentials, you can create a digital profile that securely stores your education and work history. This profile is tamper-proof and can be easily shared with potential employers. The credentials are verified using a decentralized system, meaning that there is no central authority controlling the verification process, making it more secure and transparent.
2.2 How do VCs work?
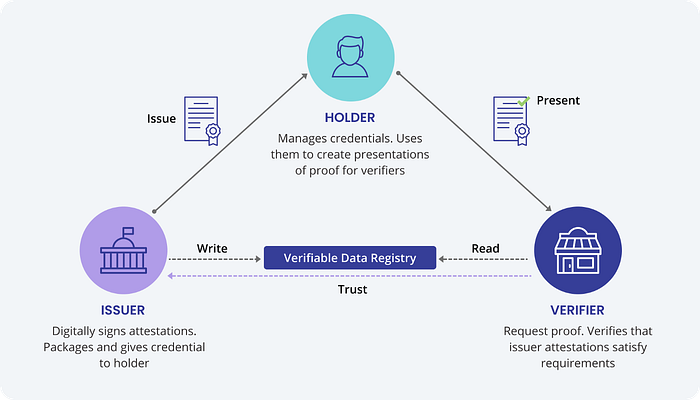
At the heart of the process, lie two important concepts: Verifiable data registries (VDRs) and Decentralized Digital Identifiers (DIDs) that work together to enable the secure and decentralized management of verifiable credentials in the web3 ecosystem. VDRs provide a decentralized way to store and manage verifiable credentials, while DIDs provide a unique and decentralized way to identify individuals and entities in the ecosystem.
Here’s how it works:
When an individual creates a verifiable credential, it is assigned a DID, which is a unique identifier that is stored on a decentralized identity network or blockchain. This DID serves as a reference to the credential and ensures that it can be securely and reliably assessed and verified by third parties. The credential itself is then stored in a VDR, which provides a tamper-proof and transparent way to manage the data.
When the individual needs to present the verifiable credential to a third party, such as an employer or educational institution, they can do so by sharing their DID with the third party. The third party can then access the VDR to retrieve and verify the authenticity of the credential. This process ensures that the individual maintains control over their personal data and prevents the need for centralized intermediaries to manage and verify the credential thereby also reducing the risk of data breaches or misuse.

2.3 The Lifecycle of Verifiable Credentials
The lifecycle of verifiable credentials can be broken down into four main stages: Issuance, Presentation, Verification, and Revocation.
Let’s explore each of them in detail!
2.3.1 Issuance
The first stage involves the creation and issuance of the verifiable credential by the issuing authority. This may involve the verification of the individual’s identity and qualifications, as well as the inclusion of any relevant metadata or attributes.
- To issue a VC, the first step is to create a DID for the individual or project. This involves generating a public and private key pair, with the public key forming the DID.
- After the DID is created, the next step is to store the relevant data in a Verifiable Data Registry (VDR) which enables data to be stored in a tamper-proof and immutable way, ensuring that it cannot be altered or deleted without permission.
- When the data is stored in the VDR, the issuer can then create the verifiable credential. This involves digitally signing the credential with the issuer’s private key, which generates a tamper-proof signature that can be used to verify the credential’s authenticity.
Once the credential is issued, it is stored securely in the individual’s digital wallet.
2.3.2 Presentation
The second stage occurs when the individual needs to present their verifiable credentials to a third party, such as a leading web3 project that houses dApps. The individual selects the relevant credentials from their digital wallet and presents them to the third party for verification. The third party then verifies the authenticity of the credentials using a decentralized identity network or blockchain.
2.3.3 Verification
This stage involves checking the validity of the verifiable credential by a third party, for example a potential employer. The third party verifies the authenticity of the credential and checks that it has not been tampered with or revoked. For this purpose, they first retrieve the verifiable credential from the individual, then check the digital signature and ensure that it matches the public key of the issuing authority and also verify attributes contained within the credential.
If the verification is successful, the third party can rely on the credential for the purpose of making decisions or granting access to services.
2.3.4 Revocation
The final stage only takes place when a verifiable credential needs to be revoked, such as in the case of fraud or inaccuracy. The issuing authority can revoke the credential, which is then immediately reflected in the individual’s digital wallet and any third-party verifications.
2.4 What types of Verifiable Credentials are there?
There are two types of verifiable credentials: Self-issued and Third-party issued.
Self-issued credentials are created by the individual themselves and are stored in their digital wallet. The individual creates a Decentralized Digital Identifier (DID), which is a unique identifier that is used to establish a verifiable link between their identity and associated credentials. The individual then creates a verifiable credential that contains information about their identity and qualifications, such as their name, date of birth, and educational qualifications. The credential is digitally signed with the individual’s private key, which generates a tamper-proof signature that can be used to verify the credential’s authenticity. The self-issued credential is stored on the individual’s device or in their digital wallet, ready to be presented whenever needed.
Third-party issued credentials, on the other hand, are issued by a trusted third-party, such as a government or educational institution. The third-party could either create a DID for the individual and store the relevant data in a Verifiable Data Registry (VDR or use the DID an individual already has. The third-party then creates a verifiable credential containing the individual’s identity and qualifications, digitally signs it with their private key, and stores it in the individual’s digital wallet. The individual can then present the credential whenever needed, and the credential can be verified using the third-party’s public key.
While both types of credentials, are able to ensure data control, security, and transparency, the efficacy of each largely depends on the specific use case and context of the credential. Self-issued credentials offer individuals greater control over their personal data and enable them to manage and share their credentials directly with third parties. This can be particularly beneficial in contexts where individuals have limited access to traditional forms of identity documentation, or where they want to maintain greater privacy and control over their personal data.
On the other hand, third-party issued credentials are often seen as more trustworthy by third parties, as they are issued by recognized authorities and can be verified using established standards and processes. This can be particularly important in contexts where security and trust are critical, such as in financial services, healthcare, or government services.
3. Verified Credentials, NFTs, Soulbound Tokens — All the same?
Verified Credentials, NFTs (Non-Fungible Tokens), and Soulbound Tokens are all different types of digital tokens; each with a unique purpose in the web3 ecosystem. While all three of these types of tokens are based on blockchain technology and share some similarities, they differ in their purpose, design, and use cases. While NFTs are focused on representing unique digital assets that can be bought, sold, or traded, Verifiable Credentials are focused on creating a secure and decentralized way of verifying an individual’s identity or credentials. Meanwhile, Soulbound Tokens enable the creation of unique and non-transferable virtual assets that are tightly linked to a specific user or account, and that cannot be duplicated or copied.
Let’s elaborate on the differences further.
- NFTs are typically stored on a blockchain as a unique digital asset, with ownership of that asset represented by ownership of the corresponding token. The token is cryptographically secure and unique, which means that it can be transferred or sold without the need for a trusted third party to validate the transaction. This is what makes NFTs so useful in the context of digital art where they allow artists to prove ownership and authenticity of their work, and collectors to buy and sell these digital assets on a global scale.
- In contrast, Verifiable Credentials’ purpose is to provide a decentralized way of verifying an individual’s identity or credentials. Verifiable Credentials use a combination of public-private key cryptography and decentralized identifiers (DIDs) to create a tamper-proof record of an individual’s credentials that can be shared and verified without the need for a centralized authority.
- Marking a difference from both NFTs and Verifiable Credentials, Soulbound tokens on the other hand, are a type of blockchain-based token that are designed to be “soulbound” to a particular user or account, making them non-transferable. This means that once a Soulbound token has been assigned to a specific user, it cannot be transferred or sold to another user. Soulbound Tokens are often used in web3 gaming and virtual worlds, where they can be used to represent unique items, character attributes, or other virtual assets.
4. Verifiable Credentials Use-Cases
Recent statistics suggest that the adoption of Verifiable Credentials in web3 is growing rapidly. According to a report by Research and Markets, the global decentralized identity market size is expected to reach $8.9 billion by 2028, rising at a market growth of 78.5% each year. One of the most promising areas of application for verifiable credentials is in the field of DeFi payments, where they can be used to facilitate secure and efficient payments within the DeFi ecosystem. For example, a user could provide proof of ownership of a specific asset as collateral for a loan, and the lender could verify this ownership through a verifiable credential.
Other potential use cases for Verifiable Credentials include web3 gaming to prove ownership of in-game assets and DAO management for establishing the identity of members and allowing for secure voting and decision-making.
However, while Verifiable Credentials have the potential to revolutionize the way we manage and share personal data in web3, there are several challenges that inhibit their wide-scale adoption. For instance, there is currently no widely adopted standard for Verifiable Credentials, which makes it difficult for different systems to interoperate and share information. This lack of standardization also makes it harder for individuals and organizations to trust the credentials issued by different authorities. Additionally, Verifiable Credentials rely on a complex web of stakeholders, including issuers, verifiers, and users. Creating effective governance structures that enable these stakeholders to collaborate and make decisions in a transparent and accountable manner is a critical challenge.
5. The Fractal ID Solution to fast track the adoption of Verifiable Credentials
As a vertically integrated web3 identity solution provider, Fractal ID is already making significant strides in promoting the adoption of verifiable credentials in the web3 ecosystem by enabling a trustworthy exchange of information between parties without the need for a centralized authority.
With Fractal, any web3 project on any chain can leverage identity verification and is additionally empowered to meet data and regulatory standards, including GDPR compliance, as well as user verification via KYC/AML checks.

For Verifiable Credentials in particular, leveraging the Fractal ID identity stack helps address interoperability challenges that lead to fragmentation and reduced trust in the overall ecosystem. Fractal ID possesses the ability to serve as a bridge between these different systems, allowing for the seamless exchange of verifiable credentials across web3 projects across the ecosystem.
Moreover, Fractal ID technology also paves the way for more individuals and web3 projects to participate in the digital identity ecosystem by offering a user-friendly interface for managing cryptographic keys and signing verifiable credentials. This can help foster a more cohesive and trusted digital identity ecosystem, leading to increased adoption and usage of verifiable credentials.
If you are interested in exploring how our web3-native identity solutions can help you and your business, book a meeting with our team.
You can explore the topic of DIDs in greater detail by rummaging through our medium articles:
Decentralized Identity Challenges & How To Tackle Them in 2022
Decentralized Identity Use Case For DAOs
Decentralized Identity Use Case for Sybil-Resistant Quadratic Voting
