The rising regulatory compliance and security concerns is driving the growth of the identity management market, which is projected to grow from ±$13B in 2021 to ±$34B in 2028. Leveraging blockchain technology in identity management is expected to boost this growth as it brings back data ownership to the users, protecting them from exploits and fraud.
In this article, we explore why identity management is important and identify the major differences between centralized and decentralized identity management methods.
What is identity management?
Identity management, also known as identity and access management (IAM) is a set of policies, regulations, and technologies (e.g. multi factor authentication (MFA), password management tools) that enable businesses and entities to control individual’s rights to access products and services.
In a nutshell, identity management solutions identify, authenticate, and authorize users’ access to services while prohibiting unauthorized users from access.
Why is identity management important?
There are numerous reasons for why identity management is important, such as:
Protect privileged data
Organizations can protect privileged data by restricting access to specific folders, tools, and applications. For example, only HR staff can be granted access to employee and candidate data, protecting personal information from exposure, and ensuring compliance.
Minimize data breaches
According to the latest IBM research, the average cost of a data breach is ±$4M, and the top data compromised in breaches are user credentials, personal data, organization internal data, medical data, and banking data.
Leveraging IAM technologies can minimize data breaches by preventing unauthorized access to private networks.
What is the difference between centralized and decentralized identity management?
The main difference between centralized and decentralized identity management solutions is the manner in which data is stored and shared with others.
Here are the top differences between centralized and decentralized identity management solutions:
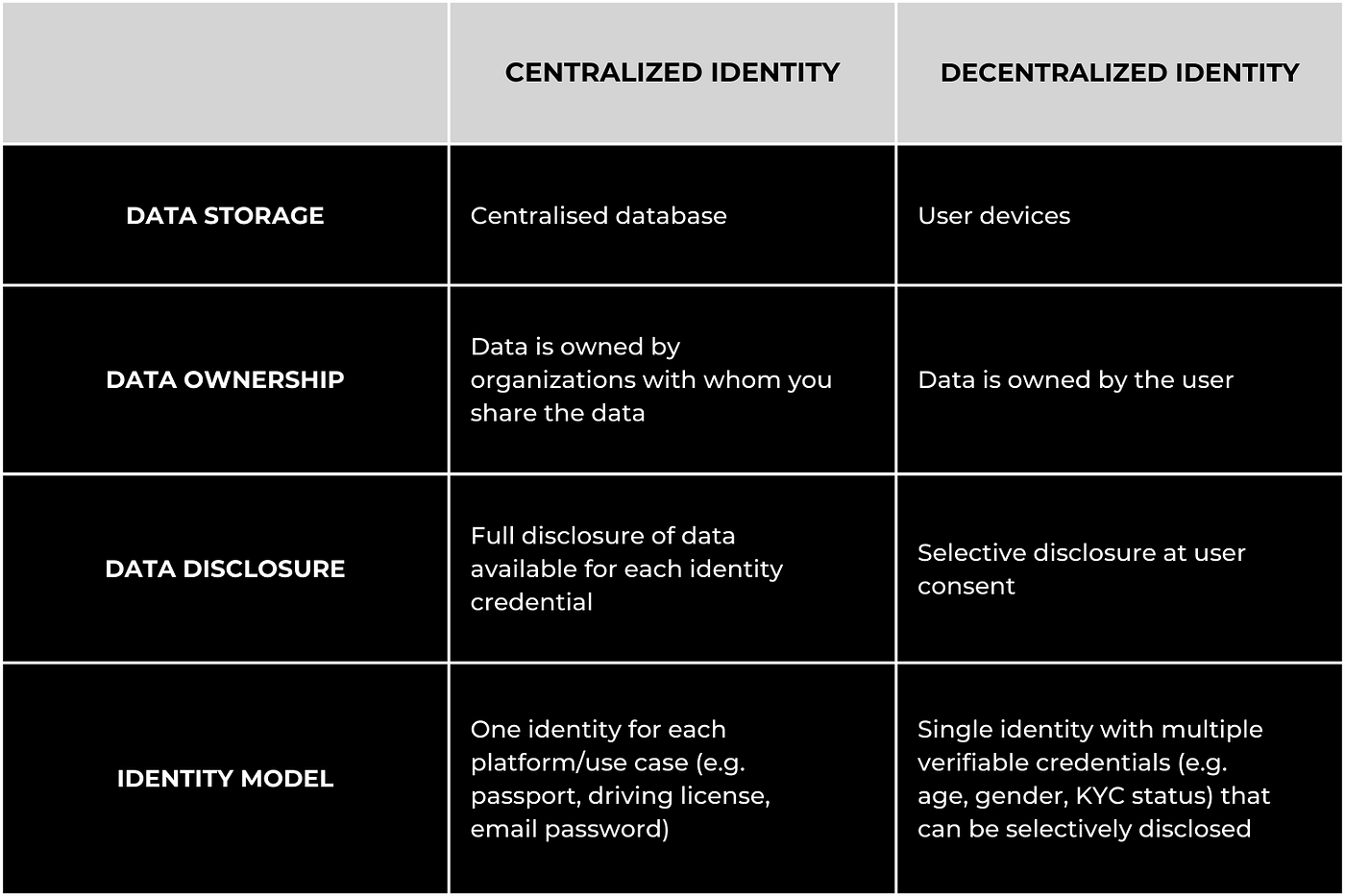
Centralized identity management technologies can ensure greater control of user access and tackle the issues of unauthorized access. However, they still fall short due to human errors which are the cause of ±82% of all data breaches in 2022.
This is where decentralized identity management can fill the gap.
In decentralized identity management solutions, users can obtain verifiable credentials about specific aspects of their identity (e.g. age, gender, KYC status) which they can selectively disclose to requesting parties. This empowers users to share data in a privacy-preserving manner.
Additionally, these credentials are stored on users’ devices and can only be accessed at user consent. This method of data storage ensures that user data is safe even if the organization, with which the data was shared, is compromised. It also ensures regulatory compliance to GDPR as organizations’ access to data is:
- At user’s consent
- Purpose limited (e.g. if the purpose is to prove a user is over 18, then a verifiable credential that proves the user’s age is enough)
What is Fractal ID?
Fractal ID is an identity verification platform, ranging from human uniqueness for sybil-resistance to KYC/AML for regulatory compliance.
Fractal ID DID credentials are automatically generated in our system after a supported KYC is approved, and these credentials can be stored on the user’s Fractal ID Wallet on the user’s device giving them complete control of their data, including support for selective disclosure.
With Fractal ID, DAOs, Launchpads, and DeFi platforms are able to maintain user’s privacy, establish safe environments for their users, and comply with data privacy regulations and standards.
